Using port-forwarding, the VNC server can be configured to only accept connections on the remote desktop ports from itself and not any external connections. If that's not an option, definitely use a strong random password and ensure that your communication to the server is encrypted. If you password is sent in plain-text, it can be intercepted. This utility will allow you to fetch and decrypt VNC passwords on a local computer system with VNC Server configured with a password. It works by fetching the encrypted password in the registry then decrypting it using the DES algorithm. The utility has two sections, Automatic Password Decryption and Custom Password Decryption. The automatic section. Look at most relevant Decrypt ultravnc password password websites out of 18.1 Thousand at KeyOptimize.com. #1 /blog/crack-or-decrypt-vnc-server-encrypted-pas. By using Password Recovery Bundle you can instantly decrypt and recover all encrypted VNC passwords from TightVNC, RealVNC, UltraVNC. How to Recover VNC Password. It is intentionally the case that an unconfigured VNC Server will not accept connections. The configuration scenarios in the following sections should give some guidelines as to what will work best for you. Maximum Security. For maximum security, you should configure the VNC server to use an encrypted connection.
Crack Or Decrypt Vnc Server Encrypted Password Using
NAME
vncpasswd− change the VNC password
Crack Or Decrypt Vnc Server Encrypted Password Windows 10
So the actual VNC user password used for encryption is: 8c4ccc2cac6cec1c (12345678 in ASCII) John The Ripper has implemented this in the version 1.9.0 Jumbo-1 In order to crack VNC passwords with hashcat we implemented this transformation with a small bash script to create a modified charset of the ascii characters.
SYNOPSIS
vncpasswd[passwd-file]
vncpasswd −f
Crack Or Decrypt Vnc Server Encrypted Password Windows 10
DESCRIPTION
vncpasswdallows you to set the password used to access VNC desktops.Its default behavior is to prompt for a VNC password andthen store an obfuscated version of this password topasswd-file (or to $HOME/.vnc/passwd if no passwordfile is specified.) The vncserver script runsvncpasswd the first time you start a VNC desktop, andit invokes Xvnc with the appropriate−rfbauth option. vncviewer can also begiven a password file to use via the −passwdoption.
The passwordmust be at least six characters long (unless the−f command-line option is used-- see below),and only the first eight characters are significant. Notethat the stored password is not encrypted securely -anyone who has access to this file can trivially find outthe plain-text password, so vncpasswd always setsappropriate permissions (read and write only by the owner.)However, when accessing a VNC desktop, a challenge-responsemechanism is used over the wire making it hard for anyone tocrack the password simply by snooping on the network.
OPTIONS
−f | Filter mode. Read a plain-textpassword from stdin and write an encrypted version tostdout. Note that in filter mode, short or even emptypasswords will be silently accepted. |
A view-onlypassword must be separated from the normal password by anewline character.
FILES
$HOME/.vnc/passwd
Default location of the VNCpassword file.
SEE ALSO
vncviewer(1),Xvnc(1) vncconfig(1), vncsession(8)
https://www.tigervnc.org
AUTHORS
TristanRichardson, RealVNC Ltd., Antoine Martin, D. R. Commanderand others.
VNC wasoriginally developed by the RealVNC team while at OlivettiResearch Ltd / AT&T Laboratories Cambridge. TightVNCadditions were implemented by Constantin Kaplinsky. Manyother people have since participated in development, testingand support. This manual is part of the TigerVNC softwaresuite.
Vnc Server Free
Since figuring out how to connect to my home machine using plain, old, VNC over a separate Secure SHell (SSH) tunnel, a few people have asked me to document the procedure so that they may easily implement it themselves. I, myself, have been known to forget some of the steps involved, so this is for my benefit as much as theirs.
In these instructions I will use the term “home PC” for the computer whose screen you wish to access from a remote location, and “remote PC” for the computer that you will use to connect to your home PC. I will assume that you know how to download and unzip files, use a command prompt, and troubleshoot minor problems pertaining to your own environment along the way.

What you will need
- TightVNC – the viewer and server that I use. You might prefer another version, however my instructions may not be entirely suitable. There is a version of VNC that seems to handle encryption all by itself, called [email protected] (how irritating is that bloody at-symbol in the name?), but I haven’t checked it out yet. Theoretically, this might be all you need to VNC with safety, but I’m set in my ways and don’t feel like fixing something that ain’t broke.
- OpenSSH for Windows – the secure shell server on your home PC that listens for incoming shells and TCP/IP tunnels within those shells.
- PuTTY – the free telnet/SSH client used to establish a secure connection with the OpenSSH server on your home PC and tunnel VNC traffic through the secure shell.
These instructions apply to the following versions using Windows XP, unhindered by any Service Pack 2 evilness:
- TightVNC version 1.2.9
- OpenSSH for Windows 3.8.1p1-1
- PuTTY release 0.56
Install the OpenSSH server on your home PC
OpenSSH for Windows is a free, Windows, implementation of the SSH protocol developed by the OpenBSD folks. SSH allows you to connect to another computer just like a telnet session, except that it is encrypted. However, SSH can also port forward (or tunnel) TCP/IP connections, which allows practically anything to be wrapped within the shell and transmitted securely (more information can be found in this SecurityFocus article).
- Double-click on the
setupssh.exeOpenSSH for Windows binary installer and accept all defaults. - Open a command prompt and change to the OpenSSH installation directory.
- Change to the
bindirectory. - Add security groups on the home PC to the group permissions file by typing:
mkgroup -l >> ..etcgroup - Add users on the home PC to the password file by typing:
mkpasswd -l >> ..etcpasswd - Enable TCP forwarding by opening the
etcsshd_configfile in the OpenSSH installation directory and removing the hash symbol (“#”) before this line:AllowTcpForwarding yes. - Make sure that any software or hardware firewalls you have allow incoming connections on port 22, the default port used by the SSH protocol. If you need to use a different port, remove the hash symbol and edit this line accordingly:
Port 22. - Save the changes to etcsshd_config then start the OpenSSH server by typing:
net start opensshd(or by starting the “OpenSSH Server” service in the Administrative Tools, Services, applet in the Control Panel).
Install the TightVNC Server on your home PC

- Double-click on the
tightvnc-1.2.9-setup.exeinstaller and accept all defaults. If you want the TightVNC Server to run automatically, tick theRegister TightVNC Server as a system serviceandStart or restart TightVNC servicecheck boxes. - If you did not enable the two check boxes mentioned above, click on Start, Programs, TightVNC, Launch TightVNC Server to open the VNC server settings window.
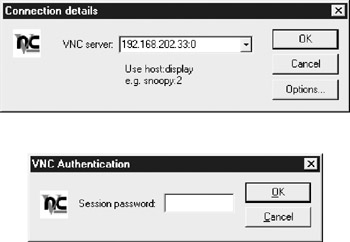
- Specify a password for incoming connections.
- Click the
Advancedbutton and enable theAllow loopback connectionscheck box. This means that the VNC server will allow your home PC to connect to itself. Why? Because the VNC Viewer session on the remote PC is being transmitted within the encrypted SSH tunnel and released onto your home PC as if you were actually there in person. This is why the VNC server needs to allow connections that would otherwise be pointless. - Unless you know what you’re doing or require a specific change, click the
OKbutton to begin accepting VNC connections.
Configure PuTTY on the remote PC and begin tunnelling
- Double-click on
putty.exeand enter theHost Name (or IP address)of your home PC. - Type a name in the
Saved Sessionsfield, such as “Home PC”. - Click on the
Connection,SSH,Tunnelscategory in the left column. - Type
5900for the source port. - Type
localhost:5900for the destination. - Click the
Addbutton. - Click on the
Sessioncategory at the top of the left column again. - Click the
Savebutton to save this configuration. - Click the
Openbutton to connect to your home PC. - Enter the username and password of the login that you use on your home PC. If your computer logs you in automatically when you start Windows, open the User Accounts applet in the Control Panel and specify a password; this also means that you must enter this password to log into Windows each time you reboot).
Install the TightVNC Viewer on the remote PC
- Double-click on the
tightvnc-1.2.9-setup.exeinstaller, deselect the TightVNC Server check box, and accept all other defaults. - Click on
Start,Programs,TightVNC,TightVNC Viewer - In the VNC Server field, accept the default of
localhost:0. This might, at first, seem strange but VNC translates display numbers to corresponding IP ports -e.g., 0 becomes 5900, 1 becomes 5901 and so on (unless you change the defaults). - Click OK to connect to the screen on your home PC.
Feel free to post comments about improvements or alternatives to this method. Please do not ask for help with troubleshooting any of the above as I do not have the time; my friends and I have all replicated the above quite successfully. If you have Windows XP with Service Pack 2, unblock port 22 on your home PC. Anything else, good luck :-)